Objectives
In this project, the Keylogger Surveillance System is used for monitoring every action that the computer has produced and based on the action, report to the user and react to the situation. To implement the system, the following tasks will be achieved. The tasks include the monitoring functions, web-based configuration function, quick configuration function, reporting function, and data analyzing function. In addition, the system will be able to operate in different operating system including Windows, Mac and Linux.
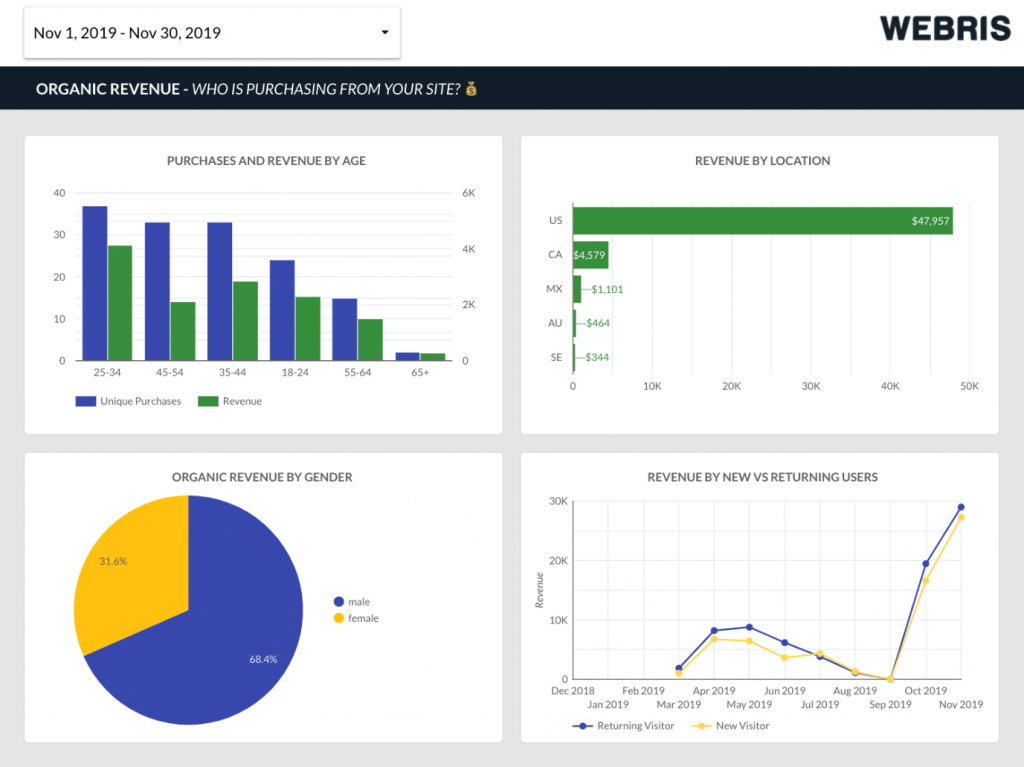
Element 1: Monitoring Functions
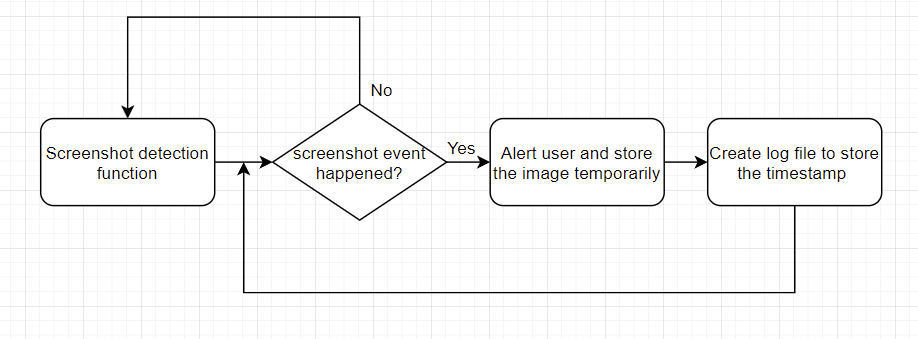
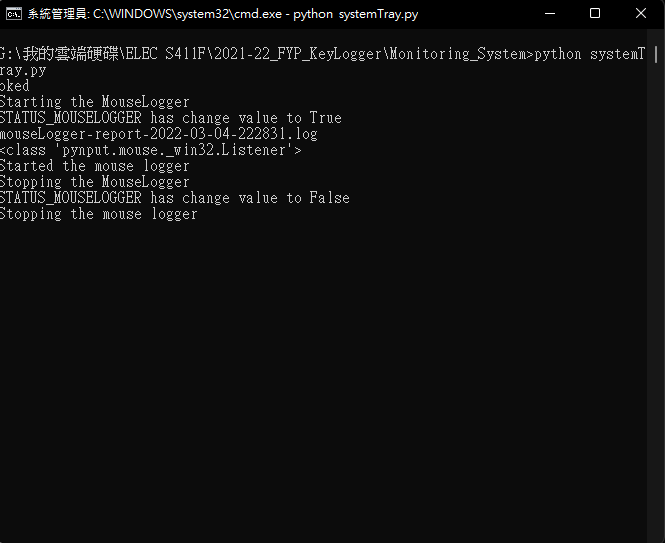
To monitor the action aspect, the application would be able to record the keystrokes, mouse movement, packet send and receive, screen capture, webcam usage
For keystrokes, the system would identify suspicious combination of keystrokes, large amounts of keystrokes in small amount of time or user custom combination of keystrokes. Normally, the system will only record the problematic keystrokes logs instead of all keystrokes. This could prevent leaking user's privacy and avoid keeping useless data.
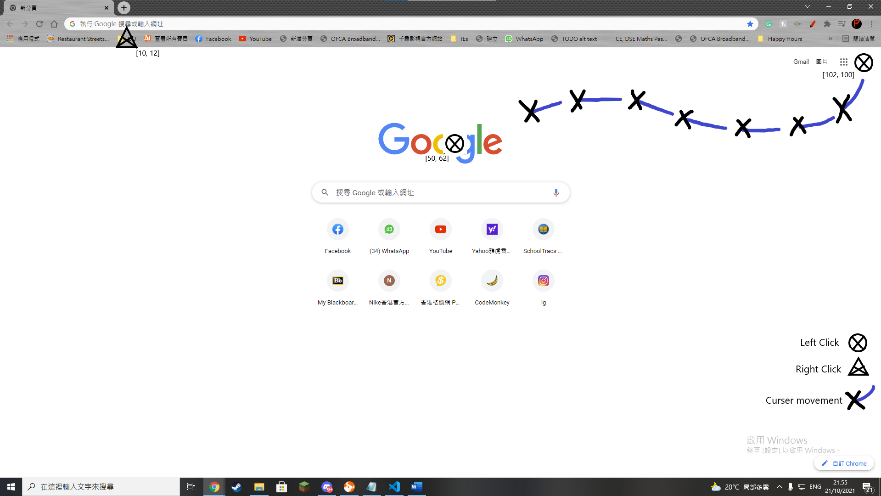
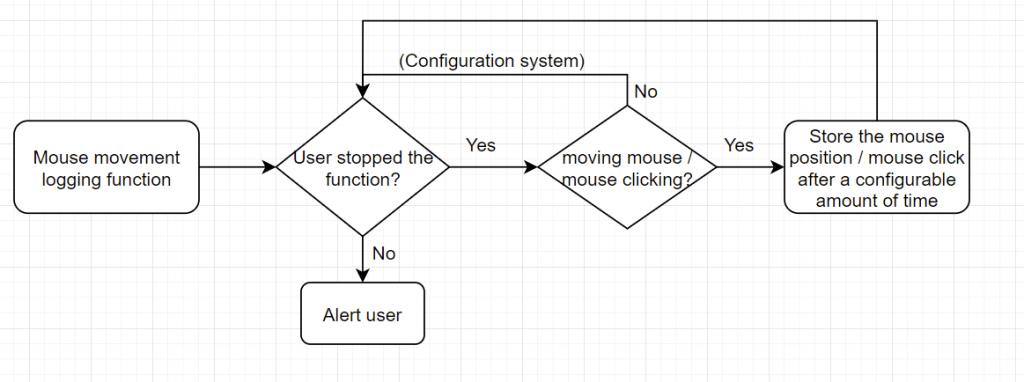
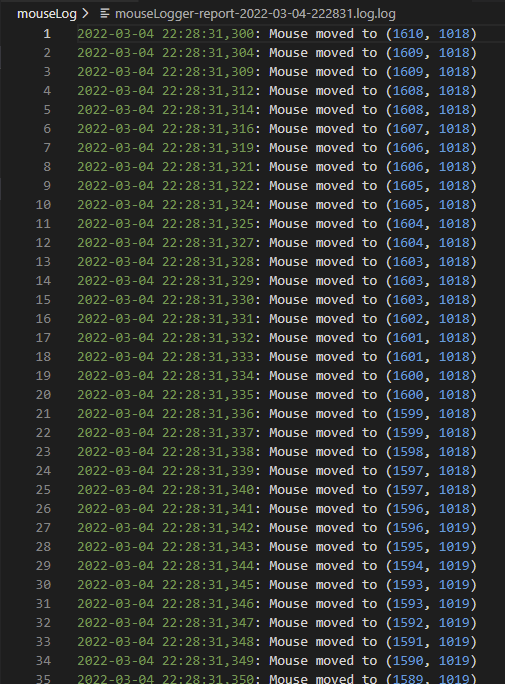
For mouse movement, the system will mark the movement on a screen capture of the present state and indicate the mouse movement and mouse click position. In the meantime, there will be a text only log for further analysis of the data.
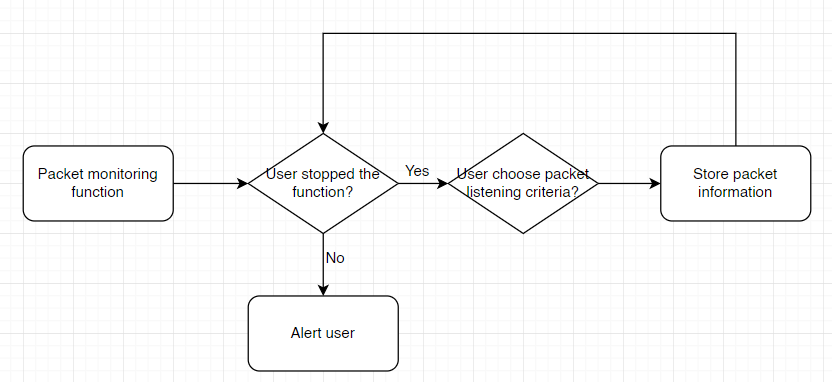
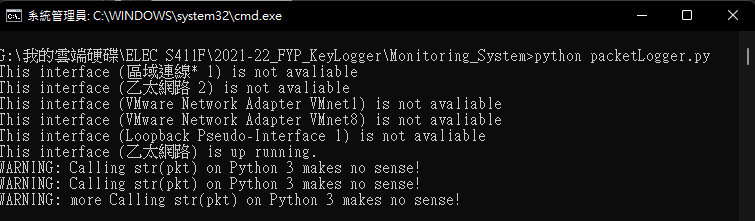
For the packet send and receive monitoring, the system could record suspicious packet send or receive by the computer. The system will continuously monitor the traffic of the computer and if suspicious traffic is discovered, the system will alert and log down the packet destination or origin for further investigation. Users are able to set up whitelist and blacklist for specific destination or origin to check and identify wanted or unwanted traffic.
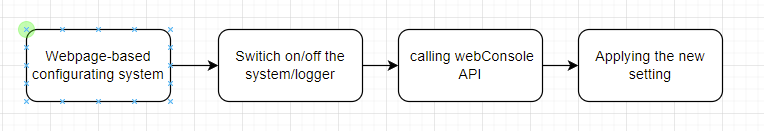
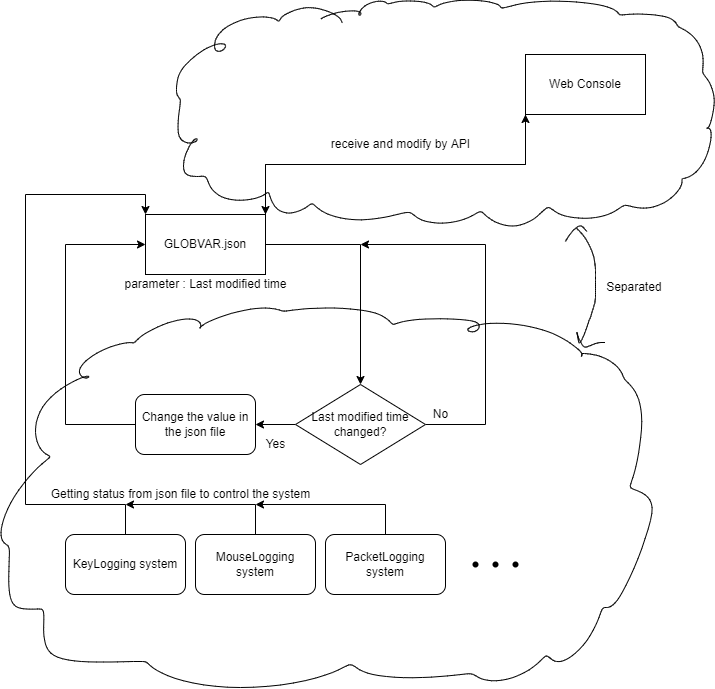
Element 2: Web-based Configuration function
To simplify the configuration progress and enhance the modifiability of the system, the Web-based configuration function will be implemented into the system. This element can provide a GUI for user to do configuration to the system, including switching on and off for each monitoring functions, parameters of every monitoring function, and viewing reports and logs file with better readability. The Web-based Configuration function will require authorization in order to access the configuration panel to improve privacy.
Element 3: Quick Configuration function
Beside the web-based configuration function, a quick configuration function would be implemented to the system as well. This function serves a purpose of providing a quicker setup change option for users. Rather than login to the web-based configuration panel, a setup button will locate in the system tray and there will be quick setup change option provided for user, such as turning on or off for monitoring function, minor change to some parameter of some monitoring function.
Element 4: Reporting function
To alert and report to the user of suspicious and emergency events within the system, there will be an online reporting functions implement to the Keylogger Surveillance System.
The online reporting function is responsible for alerting through online method. Online method includes emailing and messaging will be available for doing alert to user. This function provides way to alert user even if user is not physically located near the system. Emailing and messaging could work as a record or log for user to review and alert of what happened to their system.
Also, the log file format and encryption provide a better security and readability of the log file. The log files are responsible for storing the data that log from the logger functions but also it provides a way for user and the system to analyze and review the traces of the system. As the sensitive data may store in the log file, the file encryption of the log file is very essential to protect the user information.